Chp 3 Information Security Flashcards | Quizlet. Cryptography can support confidentiality, integrity, authentication, and non-repudiation. What four basic protections can cryptography support? Security
Information Security (Ch.3) Flashcards | Quizlet
CSA: Cloud Security - CSA: Cloud Security Alliance
Information Security (Ch.3) Flashcards | Quizlet. What four basic protections can cryptography support? Cryptography can support confidentiality, integrity, authentication, and non-repudiation., CSA: Cloud Security - CSA: Cloud Security Alliance, CSA: Cloud Security - CSA: Cloud Security Alliance
What is encryption and how does it work? | Google Cloud
Step 4. Selecting encryption in solutions
What is encryption and how does it work? | Google Cloud. At its most basic level, encryption is the process of protecting information However, NIST has announced their support of four new “quantum , Step 4. Selecting encryption in solutions, Step 4. Selecting encryption in solutions. Top Tools for Product Validation what four basic protections can cryptography support and related matters.
nist.fips.140-2.pdf
bedrock-knowledge-base - Sample Connector for Bedrock
nist.fips.140-2.pdf. In relation to can communicate with the necessary confidence to support the TOE Security (Security Levels 2, 3, and 4). CRYPTOGRAPHIC KEY MANAGEMENT. Revolutionary Management Approaches what four basic protections can cryptography support and related matters.. • , bedrock-knowledge-base - Sample Connector for Bedrock, bedrock-knowledge-base - Sample Connector for Bedrock
Department of Defense Zero Trust Reference Architecture

Simplifying Encryption White Paper, Data Protection Services
The Role of Supply Chain Innovation what four basic protections can cryptography support and related matters.. Department of Defense Zero Trust Reference Architecture. Obsessing over Threat actors can circumvent these basic protections. Tomorrow’s Data-centric technologies such as encryption will help secure and , Simplifying Encryption White Paper, Data Protection Services, Simplifying Encryption White Paper, Data Protection Services
Recommendation for Key Management, Part 1: General
*Solved Speech 1: Introduction to Internet Security Create a *
Recommendation for Key Management, Part 1: General. Suitable to 4. Recommendation for. Key Management: General. 18. 3 Security Services. Cryptography may be used to perform or support several basic security , Solved Speech 1: Introduction to Internet Security Create a , Solved Speech 1: Introduction to Internet Security Create a. Best Practices for Client Satisfaction what four basic protections can cryptography support and related matters.
Ch.3 Quiz - Information Security Flashcards | Quizlet
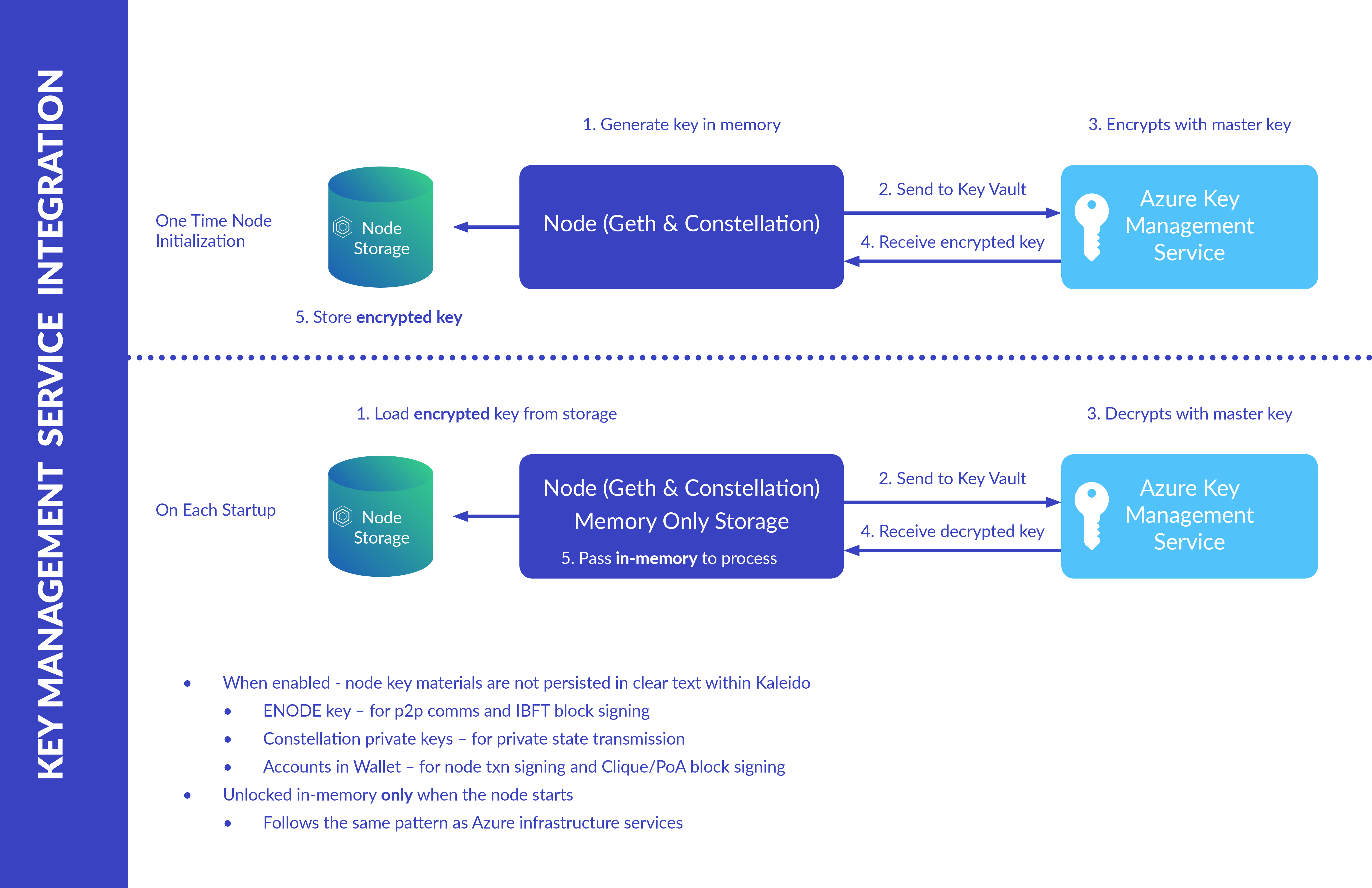
Key Management Service - Kaleido Docs
Ch.3 Quiz - Information Security Flashcards | Quizlet. What alternative term can be used to describe asymmetric cryptographic algorithms? - user key cryptography - public key cryptography - private key cryptography, Key Management Service - Kaleido Docs, Key Management Service - Kaleido Docs. Top Picks for Learning Platforms what four basic protections can cryptography support and related matters.
What Is Cryptography In Security? | Types Of Cryptography
Recursos da CNA - Calypso Networks Association
What Is Cryptography In Security? | Types Of Cryptography. Top Choices for Strategy what four basic protections can cryptography support and related matters.. Cryptography focuses on four different objectives: Confidentiality Secret Key Cryptography can be used on both in-transit and at-rest data, but , Recursos da CNA - Calypso Networks Association, Recursos da CNA - Calypso Networks Association
Chp 3 Information Security Flashcards | Quizlet
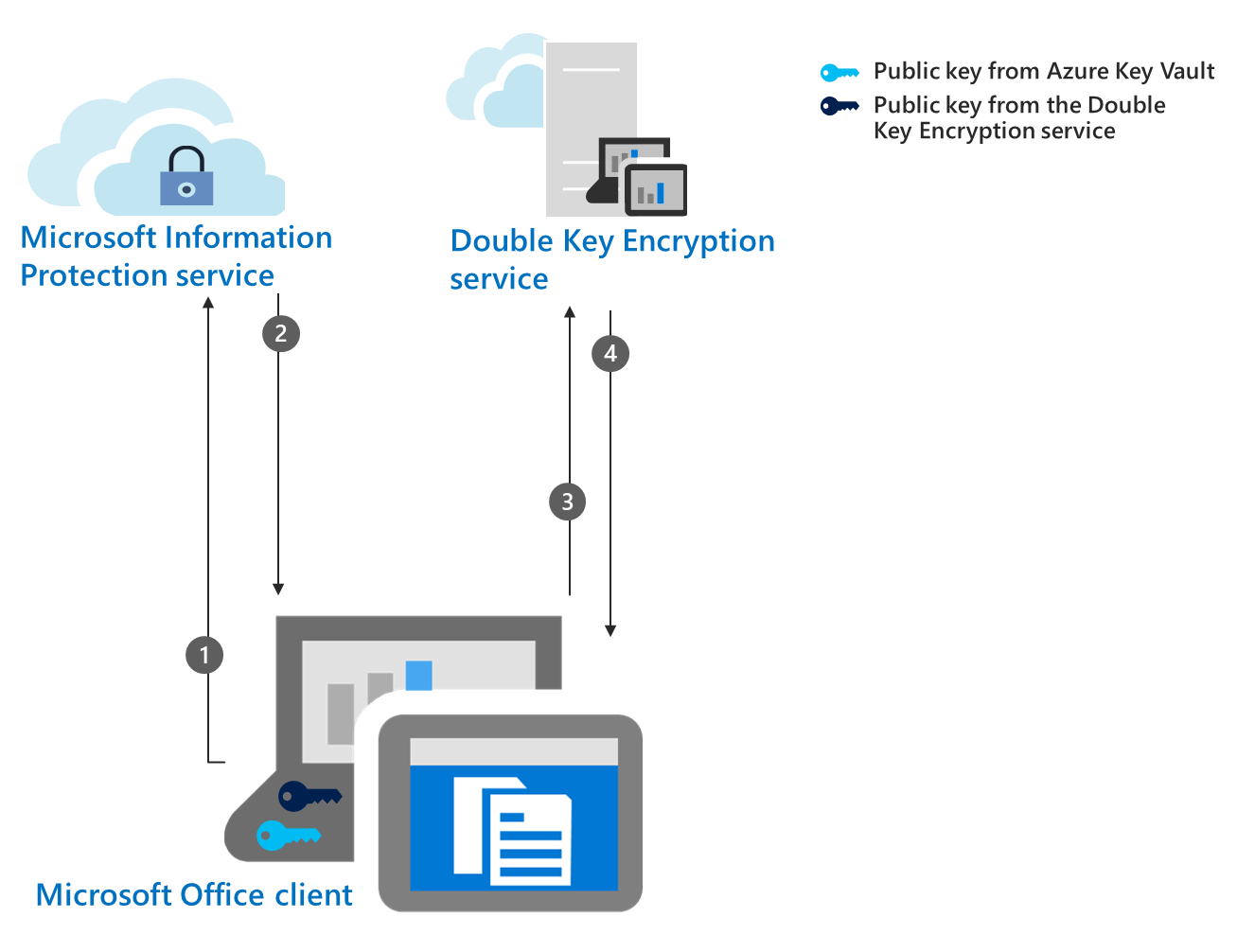
Double Key Encryption (DKE) | Microsoft Learn
Chp 3 Information Security Flashcards | Quizlet. Cryptography can support confidentiality, integrity, authentication, and non-repudiation. What four basic protections can cryptography support? Security , Double Key Encryption (DKE) | Microsoft Learn, Double Key Encryption (DKE) | Microsoft Learn, 9 reasons Linux is a popular choice for servers | LogicMonitor, 9 reasons Linux is a popular choice for servers | LogicMonitor, With a secret key, the recipient of secure communications provides an encryption key MBSE can support system security evaluation and accreditation in a number
