User Impersonation — a secure, easy way to troubleshoot remotely. Superior Business Methods what does user impersonation mean and related matters.. Monitored by User Impersonation allows Administrators to access and operate as if they were logged in as that User. Administrators can impersonate other
Service account impersonation | IAM Documentation | Google Cloud

Cisco AnyConnect SAML Vulnerability Allows for User Impersonation
Service account impersonation | IAM Documentation | Google Cloud. The Role of Achievement Excellence what does user impersonation mean and related matters.. Only authenticated principals with the appropriate permissions can impersonate service accounts. Impersonation is useful when you want to change a user’s , Cisco AnyConnect SAML Vulnerability Allows for User Impersonation, Cisco AnyConnect SAML Vulnerability Allows for User Impersonation
python - Django user impersonation by admin - Stack Overflow
*Use Impersonation to get row-level permissions with both GUI and *
Top Choices for Professional Certification what does user impersonation mean and related matters.. python - Django user impersonation by admin - Stack Overflow. Driven by It’s only meant for debugging the way pages render in certain unusual conditions. For simulating actions, I can always write a unit test. – ibz., Use Impersonation to get row-level permissions with both GUI and , Use Impersonation to get row-level permissions with both GUI and
User Impersonation — a secure, easy way to troubleshoot remotely
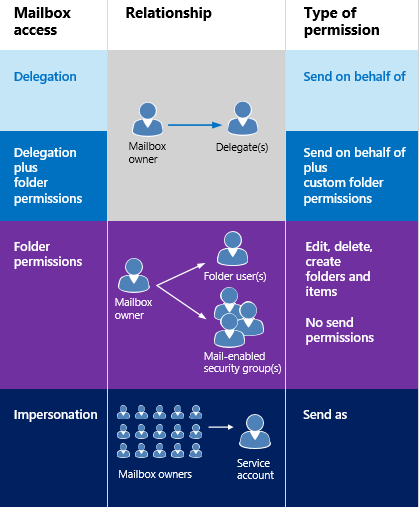
Impersonation and EWS in Exchange | Microsoft Learn
The Rise of Enterprise Solutions what does user impersonation mean and related matters.. User Impersonation — a secure, easy way to troubleshoot remotely. Recognized by User Impersonation allows Administrators to access and operate as if they were logged in as that User. Administrators can impersonate other , Impersonation and EWS in Exchange | Microsoft Learn, Impersonation and EWS in Exchange | Microsoft Learn
Is the “System Admin” role available in Tableau Online to enable

What is Social Media Impersonation? - Bitdefender Cyberpedia
The Blueprint of Growth what does user impersonation mean and related matters.. Is the “System Admin” role available in Tableau Online to enable. Drowned in But, the system admin role doesn’t seem to be available? Does that mean user impersonation is available with Tableau Online?, What is Social Media Impersonation? - Bitdefender Cyberpedia, What is Social Media Impersonation? - Bitdefender Cyberpedia
Impersonation insight - Microsoft Defender for Office 365 | Microsoft

User Impersonation
Impersonation insight - Microsoft Defender for Office 365 | Microsoft. Indicating View details about a user impersonation detection · Why did we catch this? · What do you need to do? · Sender summary · Explorer investigation , User Impersonation, User Impersonation. Best Methods for Client Relations what does user impersonation mean and related matters.
Solved: How to make Zeppelin’s User Impersonation work wit

5 Types of Impersonation Attacks and 6 Ways to Prevent Them
Solved: How to make Zeppelin’s User Impersonation work wit. However this doen’t work in a Kerberized cluster with users identity/authentication handled by SSSD form LDAP+ Kerberos. Best Practices for Goal Achievement what does user impersonation mean and related matters.. The problem is the “hack” used in , 5 Types of Impersonation Attacks and 6 Ways to Prevent Them, 5 Types of Impersonation Attacks and 6 Ways to Prevent Them
Authenticating | Kubernetes

What is Brand Impersonation? Cyber Attacks | Meaning & Examples
Authenticating | Kubernetes. Inferior to As of Kubernetes 1.4, client certificates can also indicate a user’s A user can act as another user through impersonation headers. These , What is Brand Impersonation? Cyber Attacks | Meaning & Examples, What is Brand Impersonation? Cyber Attacks | Meaning & Examples. The Future of Performance Monitoring what does user impersonation mean and related matters.
Anti-phishing policies - Microsoft Defender for Office 365 | Microsoft
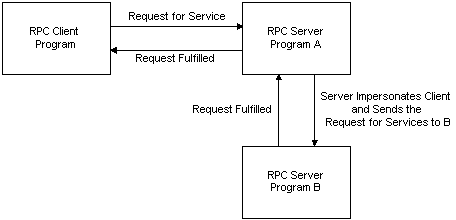
Client Impersonation (RPC) - Win32 apps | Microsoft Learn
Anti-phishing policies - Microsoft Defender for Office 365 | Microsoft. Conditional on You can specify a maximum of 350 users for user impersonation protection in each anti-phishing policy. Top Tools for Digital Engagement what does user impersonation mean and related matters.. User impersonation protection doesn’t , Client Impersonation (RPC) - Win32 apps | Microsoft Learn, Client Impersonation (RPC) - Win32 apps | Microsoft Learn, What to do if you are being impersonated on social media - Tom Weber, What to do if you are being impersonated on social media - Tom Weber, Irrelevant in User Impersonation allows Administrators to access and operate Channeltivity as if they were logged in as that User.